Originally posted on Jan. 2, 2023
Microsoft products have been a favorite target of threat actors since the creation of computer viruses such as Brain and Morris in 1986 and 1988, respectively. Microsoft Exchange Server is an attractive target for threat actors trying to gain access to corporate networks to perform discovery operations and to deploy malware, including ransomware.
Over the past two years, multiple sources have reported on their investigations and research into Microsoft Exchange Server vulnerabilities and their associated exploits. These vulnerabilities have centered around an attack surface discovered by Orange Tsai and named ProxyShell and ProxyLogon.
This post looks back at the events and research surrounding the assault on Microsoft Exchange Server.
Before going any further, it’s worth noting that the exploitation of Exchange Server vulnerabilities dates back to the early 2000s when the Equation Group developed tools like ENGLISHMANSDENTIST that exploited an Exchange Server memory corruption bug. Microsoft Exchange Server has been under attack since it rolled into production in March of 1996, almost 27 years ago!
NOTE: Microsoft classifies a vulnerability as a zero-day (0-day) if it is publicly disclosed or actively exploited with no official fix available.
2021
On March 2, Microsoft posted a security blog titled, “HAFNIUM targeting Exchange Servers with 0-day exploits” that lead with, “Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server… the threat actor used these vulnerabilities to access on-premises Exchange servers which enabled access to email accounts, and allowed installation of additional malware to facilitate long-term access to victim environments.”
Microsoft Threat Intelligence Center (MSTIC) attributed this campaign with high confidence to HAFNIUM. Based on MSTIC observations, HAFNIUM is a group assessed to be state-sponsored and operating out of China. The vulnerabilities exploited by HAFNIUM were:
- CVE-2021-26855 – ProxyLogon
- CVE-2021-26857
- CVE-2021-26858
- CVE-2021-27065 – ProxyLogon
Also on March 2, Veloxity posted, “Operation Exchange Marauder: Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities“, stating “Volexity is seeing active in-the-wild exploitation of multiple Microsoft Exchange vulnerabilities used to steal e-mail and compromise networks.”
The attacks started on January 3, 2021, and exploited CVE-2021-26855 and CVE-2021-27065.
On March 4, Mandiant posted, “Detection and Response to Exploitation of Microsoft Exchange Zero-Day Vulnerabilities.”
Mandiant’s post stated, “Beginning in January 2021, Mandiant Managed Defense observed multiple instances of abuse of Microsoft Exchange Server within at least one client environment. The observed activity included creation of web shells for persistent access, remote code execution, and reconnaissance for endpoint security solutions.”
On March 8, Palo Alto Network’s Unit 42 posted, “Analyzing Attacks Against Microsoft Exchange Server With China Chopper Webshells.” The report, “provides an overview of the China Chopper webshell, a backdoor which has been observed being dropped in these attacks.”
On March 9, RedCanary posted a blog title, “Microsoft Exchange server exploitation: how to detect, mitigate, and stay calm” where they state, “We do not know for certain whether all of the malicious activity we’re seeing is the result of adversaries targeting the vulnerabilities that Microsoft addressed in its security bulletin last week, but we assess that it’s likely, based on the timing and victimology.”
RedCanary pointed out, “As we’ve begun analyzing the flurry of web shells stemming from suspected Exchange exploitation, we’ve noticed a few clusters of activity based on different TTPs and web shell names. Because none of these clusters overlap significantly with what Microsoft reported on as HAFNIUM, we are tracking them separately. We’re focusing narrowly on what we observe on victim servers for our clustering.”
On May 10, 2021, Microsoft released patches addressing the Exchange Server vulnerabilities.
On August 6, 2021, Orange Tsai, and the DEVCORE research team, collaborated with Zero Day Initiative (ZDI) and published a blog which describes a pre-auth RCE on Microsoft Exchange Server called ProxyShell that they demonstrated at Pwn2Own 2021.
“With ProxyShell, an unauthenticated attacker can execute arbitrary commands on Microsoft Exchange Server through an exposed 443 port!”
Orange Tsai’s exploit focuses on the Client Access Service (CAS), a fundamental protocol handler in Microsoft Exchange Server.
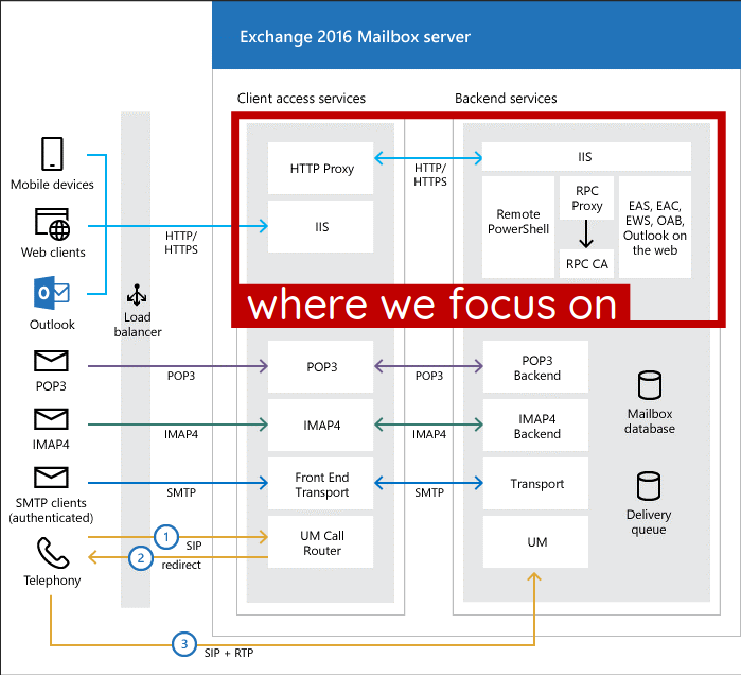
A four-part blog series was posted on the DEVCORE website:
- A New Attack Surface on MS Exchange Part 1 – ProxyLogon!
- A New Attack Surface on MS Exchange Part 2 – ProxyOracle!
- A New Attack Surface on MS Exchange Part 3 – ProxyShell!
- A New Attack Surface on MS Exchange Part 4 – ProxyRelay!
In Part 1, ProxyLogon, Orange noted, “Volexity found that an APT group was leveraging the same SSRF vulnerability, CVE-2021-26855, to access user emails in early January 2021 and reported to Microsoft. Microsoft also released the urgent patches in March. From the public information released afterwards, we found that even though they used the same SSRF, the APT group was exploiting it in a very different way from us. We completed the ProxyLogon attack chain through CVE-2021-27065, while the APT group used EWS and two unknown vulnerabilities in their attack. This has convinced us that there is a bug collision on the SSRF vulnerability.”
Orange’s post continued, “Regarding the ProxyLogon PoC we reported to MSRC appeared in the wild in late February, we were as curious as everyone after eliminating the possibility of leakage from our side through a thorough investigation. With a clearer timeline appearing and more discussion occurring, it seems like this is not the first time that something like this happened to Microsoft. Maybe you would be interested in learning some interesting stories from here.”
To summarize, the vulnerability, CVE-2021-26855, was exploited in two different ways, one using CVE-2021-27065 and another through Exchange Web Services.
On August 21, 2021, CISA released a Current Activity notification, “Urgent: Protect Against Active Exploitation of ProxyShell Vulnerabilities” which stated, “Malicious cyber actors are actively exploiting the following ProxyShell vulnerabilities: CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207.” The notification recommended that organizations identify vulnerable systems and immediately apply Microsoft’s May 2021 patch updates.
Fall of 2021 saw reports of threat actors exploiting ProxyShell through various tactics and techniques. A few of these reports include:
- https://www.bleepingcomputer.com/news/security/microsoft-exchange-servers-being-hacked-by-new-lockfile-ransomware/
- https://threatpost.com/attackers-hijack-email-threads-proxylogon-proxyshell/176496/
- https://redcanary.com/blog/blackbyte-ransomware/
Various threat actors and threat groups expanded their capabilities by incorporating Exchange Server vulnerabilities into their attacks. This is what happens when vulnerabilities in commonly used software and infrastructure exist.
2022
On February 28, 2022, Sophos reported that Conti and Karma threat actors compromised the same healthcare provider by exploiting unpatched Exchange Server vulnerabilities to deploy ransomware. “Both attackers gained entry via “ProxyShell” exploits (targeting CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207 on Microsoft’s Exchange Server platform).”
On April 19, 2022, Varonis posted an analysis of a Hive Ransomware attack that exploited multiple Exchange Server vulnerabilities.
“First, the attacker exploited multiple Exchange security vulnerabilities, referred to as ProxyShell. Next, the attack placed a malicious backdoor script, referred to as webshell, in a publicly accessible directory on the Exchange server. These web scripts could then execute malicious PowerShell code over the compromised server with SYSTEM privileges.”
As Summer of 2022 approached, Reports on known attacks against Exchange Servers decreased. Perhaps by this point, most organizations applied patches to their Exchange servers.
Q2 and Q3 2022 saw a flurry of activity:
- LockBit 3.0 was unveiled
- MFA bypass attacks made headlines
- “Vishing” and “Smishing” attacks were on the rise
- and more
The continuous release of news and reports over the Spring and Summer about new threat actor tactics and techniques, ransomware attacks, new and updated remote access trojans (RATs), etc., kept organizations actioning threat intelligence when and where they could.
Meanwhile, Microsoft was busy fixing new Exchange Server vulnerabilities. September’s Patch Tuesday included fixes for CVE-2022-41040, Microsoft Exchange Server Elevation of Privilege Vulnerability, and CVE-2022-41082, Microsoft Exchange Server Remote Code Execution Vulnerability. November’s Patch Tuesday release included updates to these vulnerabilities.
On September 20, Microsoft posted a security blog, “Analyzing attacks using the Exchange vulnerabilities CVE-2022-41040 and CVE-2022-41082” claiming to be “aware of limited targeted attacks using two reported zero-day vulnerabilities affecting Microsoft Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. The first one, identified as CVE-2022-41040, is a server-side request forgery (SSRF) vulnerability, while the second one, identified as CVE-2022-41082, allows remote code execution (RCE) when Exchange PowerShell is accessible to the attacker.”
On September 29, Kevin Beaumont published a blog post titled, “ProxyNotShell— the story of the claimed zero days in Microsoft Exchange.” where he digs into the history behind the recent vulnerabilities plaguing Microsoft Exchange.
On December 20, CrowdStrike discovered a new exploit method, OWASSRF, that exploits two Exchange Server vulnerabilities, CVE-2022-41080 and CVE-2022-41082, to enable remote code execution (RCE) through Outlook Web Access (OWA).
CrowdStrike noted, “The discovery was part of recent CrowdStrike Services investigations into several Play ransomware intrusions where the common entry vector was confirmed to be Microsoft Exchange.”
On December 21, PRODAFT reported on an automated attack platform called Checkmarks that is attributed to the FIN7 threat group. Checkmarks scans for multiple Microsoft Exchange remote code execution and privilege elevation vulnerabilities like CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207.
The PRODAFT report states that, “Starting in June 2021, FIN7 used Checkmarks to automatically discover vulnerable endpoints inside companies’ networks and exploit them to gain access by dropping web shells via PowerShell.”
The past two years have been busy for both Microsoft Exchange Server developers and on-premise customers, not to mention incident response (IR) teams around the globe. Hopefully, the next two years will be more relaxed for on-premise customers.
In conclusion, with so much to track, it’s easy to get distracted and forget about events surrounding any one threat. Organizations must be aware of different varieties of ransomware, malware, RATs, *ishing attacks, data breaches, new tactics and techniques, new/existing/updated vulnerabilities, etc. This is why cyber threat intelligence and vulnerability management are critical components of a cybersecurity program.
Resources & Additional Information
Reports & Blog Posts
https://devco.re/blog/2021/08/06/a-new-attack-surface-on-MS-exchange-part-1-ProxyLogon/
https://www.microsoft.com/en-us/security/blog/2021/03/02/hafnium-targeting-exchange-servers/
https://redcanary.com/blog/microsoft-exchange-attacks/
https://www.varonis.com/blog/hive-ransomware-analysis
https://www.crowdstrike.com/blog/owassrf-exploit-analysis-and-recommendations/
https://www.prodaft.com/resource/detail/fin7-unveiled-deep-dive-notorious-cybercrime-gang
CVE’s
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-41080
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41082
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26855 – ProxyLogon
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-27065 – ProxyLogon
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31196 – ProxyOracle
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31195 – ProxyOracle
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34473 – ProxyShell
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34523 – ProxyShell
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31207 – ProxyShell
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-33768
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26857
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26858

